Why cyber safety training fails. And how we fix it.
The uncomfortable truth
We're mandating cybersecurity training that makes people 18.5% more likely to fall for phishing attacks.
An entire compliance industry profits from solutions that actively harm security.
The academic evidence is overwhelming. The authorities know better. Yet we keep doubling down on failure.
Employees are no safer and organisations face cultural harm on top of cyber risk.
The current reality
Estimates put the global cost of cybercrime at roughly 10.5 trillion USD per year by 2025. That would rank as the world’s third largest economy. [1]
Phishing remains a dominant breach vector. IBM’s 2023 Cost of a Data Breach report attributes sixteen percent of all analysed breaches to phishing. [2]
Training should be the first line of defence. The evidence says otherwise.
A landmark randomised controlled study of 19,500 employees at a large healthcare organisation ran ten phishing campaigns over eight months. It assessed annual awareness modules and embedded phishing training.
The key findings are stark.
Static training made people worse at spotting phishing. The authors report that “users who complete multiple static training sessions have a 18.5% increased likelihood of failing for each additional training they complete.” [3]
Engagement often collapsed. “Between 37–51% of all training sessions have no engagement at all: users simply close the page immediately.” [3]
Even when training worked, the benefit was negligible. “On average, users in the training groups have only a 1.7% lower failure rate than those in the control group.” [3]
Their conclusion is clear. In common forms as deployed today, training is “unlikely to offer significant value relative to its considerable expense in time and effort.” [3]
Meanwhile, punitive phishing gotchas have damaged trust. GoDaddy’s fake holiday bonus test triggered public criticism and an apology [4] and in the UK, West Midlands Trains faced a backlash after a fake COVID bonus lure. [5]
What we have learnt
The leading authorities are not calling for more of the same. They emphasise layered controls, supportive culture, and measurable behaviour change.
NCSC UK warns that simulations and punishment erode trust, and that relying on users to spot every phish wastes time and money. [6]
ENISA’s guidance treats cybersecurity as a behavioural and cultural challenge, advocating human-centred approaches. [7]
NIST advocates a lifecycle learning program that encourages behaviour change, uses role-based content, and includes metrics to evaluate and improve the program. Annual checkbox modules are insufficient on their own. [8]
Academic evidence beyond the UCSD study points the same way. A 15-month, 14,000-employee study reported no positive effect and signs of harm from embedded training as commonly delivered. [9]
A controlled trial found no significant benefit from spear-phishing training. [10]
Benefit often comes from the periodic reminder rather than the content itself, which many users do not consume. [11]
Research on timing effects shows that reminder cadence matters. [12]
And yet the default is still punitive phishing. Fail a ‘phish’ and you get sent to ‘learning’.
Plus, the main reason why traditional learning fails
Cybercriminals succeed because they're psychological manipulators, they exploit human nature. They understand our hardwired responses: authority bias ("this looks official"), loss aversion ("I'll get in trouble"), and time pressure ("urgent response required").
Traditional training reinforces these exact vulnerabilities by creating anxiety around "getting it wrong" rather than building confident decision-making skills.
Instead of developing psychological resilience against manipulation, we're conditioning people to be more compliant and fearful - exactly what helps criminals.
How we fix it
Stacey Edmonds, our co-founder, experienced and recognised the problem in 2015, tested a different approach and proved that when digital safety becomes consumer-grade, enjoyable, rewarding, and measurable, people engage and they change.
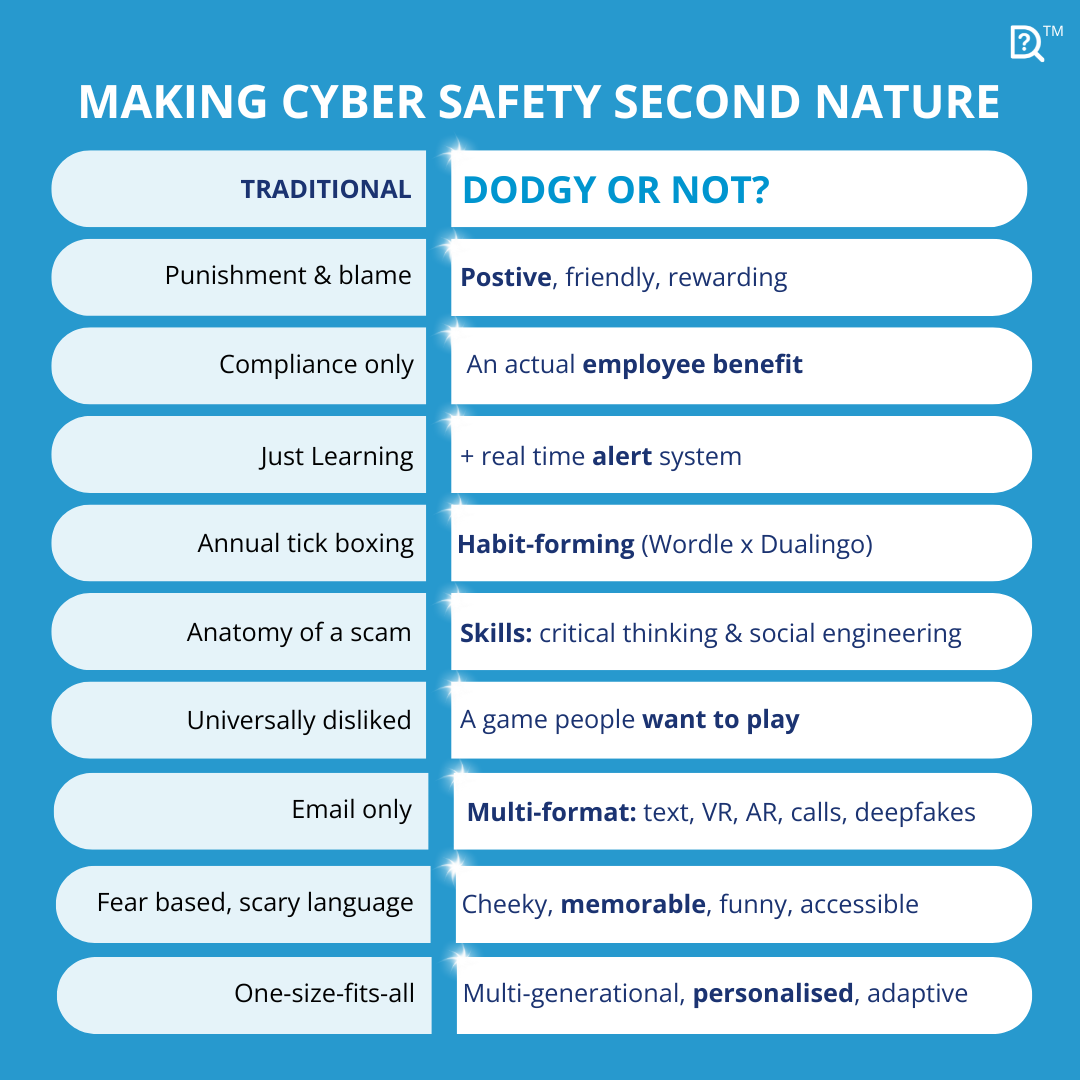
How Dodgy or Not? Changes the Game (pun intended!)
Why Dodgy or Not? works
Every element of Dodgy or Not? directly addresses what research and regulators are demanding:
1. Continuous not episodic. DailyDodgy streaks keep skills sharp with minimal time cost.
2. Positive not punitive. We replace shame with game to maintain psychological safety.
3. Behavioural not theoretical. We build instincts, not just anatomy-of-a-scam slides.
4. Multi-format and life-focused. Attacks hit home as often as work. We prepare people everywhere.
5. Personalised and adaptive. Scenarios evolve like real scams and vary by role and context.
6. Measurement that matters. Confidence, competence, instincts and reporting. Actionable evidence that auditors and regulators say is missing today.
7. Useful beyond training. Live alerts and scam signals make this a daily tool, not just a course.
The future
Cybercrime is accelerating. Human error remains the root cause. And traditional training has failed to move the dial.
The choice is stark: keep funding failure or invest in what actually works.
Would you like to learn more? See Dodgy or Not? in action
Sources and research evidence
Cybersecurity Ventures. 2023. “Cybercrime To Cost The World $10.5 Trillion Annually By 2025.” https://cybersecurityventures.com/cybercrime-damage-costs
IBM Security. 2023. “Cost of a Data Breach Report 2023.” Phishing identified as sixteen percent of breaches. https://www.ibm.com/reports/data-breach
Ho, G., Mirian, A., Luo, E., Tong, K., Lee, E., Liu, L., Longhurst, C. A., Dameff, C., Savage, S., and Voelker, G. M. 2025. “Understanding the Efficacy of Phishing Training in Practice.” IEEE Symposium on Security and Privacy. https://www.sysnet.ucsd.edu/~voelker/pubs/phishtrain-oakland25.pdf
CBS News. 25 Dec 2020. “GoDaddy apologizes for ‘insensitive’ phishing email offering bonuses to employees.” https://www.cbsnews.com/news/godaddy-apologizes-insensitive-phishing-email-bonuses-employees/
The Register. 11 May 2021. “Train operator phlunks phishing test by teasing employees with non-existent COVID bonus.” https://www.theregister.com/2021/05/11/west_midlands_trains_phishing_drill_goes_off/
National Cyber Security Centre UK. Reviewed 13 Feb 2024. “Phishing attacks: defending your organisation.” See section on problems with phishing simulations. https://www.ncsc.gov.uk/pdfs/guidance/phishing.pdf
ENISA. 2019. “Cybersecurity Culture Guidelines: Behavioural Aspects of Cybersecurity.” https://www.enisa.europa.eu/publications/cybersecurity-culture-guidelines-behavioural-aspects-of-cybersecurity
NIST Special Publication 800-50 Rev. 1. September 2024. “Building a Cybersecurity and Privacy Learning Program.” https://csrc.nist.gov/pubs/sp/800/50/r1/final
Lain, D., Kostiainen, K., and Capkun, S. 2022. “Phishing in Organizations: Findings from a Large-Scale and Long-Term Study.” IEEE Symposium on Security and Privacy. https://arxiv.org/abs/2112.07498
Caputo, D. D., Pfleeger, S. L., Freeman, J. D., and Johnson, M. E. 2014. “Going Spear Phishing: Exploring Embedded Training and Awareness.” IEEE Security and Privacy 12(1): 28–38. https://ieeexplore.ieee.org/document/6727446
Lain, D., Jost, T., Matetic, S., Kostiainen, K., and Capkun, S. 2024. “Content, Nudges and Incentives: A Study on the Effectiveness and Perception of Embedded Phishing Training.” ACM CCS. https://arxiv.org/pdf/2409.01378
Reinheimer, B., Aldag, L., Mayer, P., et al. 2020. “An investigation of phishing awareness and education over time: When and how to best remind users.” USENIX SOUPS. https://www.usenix.org/conference/soups2020/presentation/reinheimer
Verizon. 2024. “Data Breach Investigations Report 2024.” https://www.verizon.com/business/resources/reports/dbir/
University of Chicago. Grant Ho publications page for study metadata. https://people.cs.uchicago.edu/~grantho/